Tired of confusing security terms and worrying about online threats? Relax! This guide breaks down 2FA (Two-Factor Authentication) and MFA (Multi-Factor Authentication) in plain language, helping you choose the perfect shield for your online accounts. Discover best practices, easy tips, and feel confident navigating the digital world in 2024.
But wait, which defender should you choose? Both 2FA and MFA offer layers of security, but understanding their nuances is key to choosing the right shield for your needs. This comprehensive guide will equip you with the knowledge and tools to navigate the digital Wild West with confidence, leaving data breaches and identity theft in the dust.
Demystifying the Factors: 2FA vs. MFA:
Imagine your online accounts as a treasure trove, guarded by various layers of security. Both 2FA and MFA add more layers to the traditional password-based lock, significantly enhancing protection. But the key difference lies in the number of “factors” required:
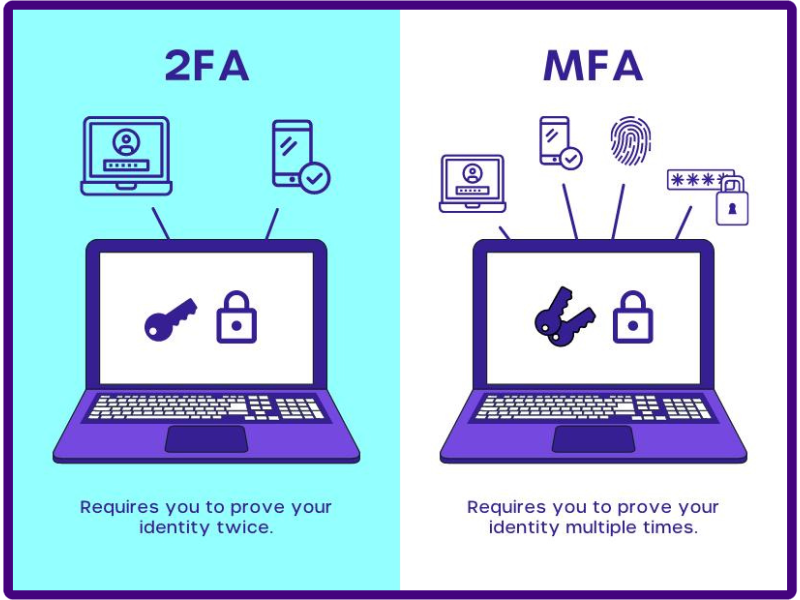
- 2FA: This method demands two distinct factors for verification. Think of it like a double lock – you need your password and another factor, like a code sent to your phone, a security token, or even fingerprint recognition.
- MFA: It leverages two or more factors for even stronger security. Picture a high-tech vault with multiple layers: password, facial recognition scan, voice recognition, and even location verification, creating a formidable barrier against intruders.
Beyond the Buzzwords: Understanding the Technology:
2FA typically employs SMS verification, one-time password (OTP) codes, push notifications, or hardware tokens. MFA, on the other hand, delves deeper into the security arsenal:

- Biometrics: Fingerprint scans, facial recognition, and even iris scans offer unique and difficult-to-replicate verification factors.
- Hardware Keys: Physical tokens that plug into your device, providing an extra layer of physical security.
- Location-based authentication: Verifies your login attempt originates from a trusted location, adding another layer of protection against remote attacks.
- Risk-based assessments: Analyzes login attempts for suspicious activity, dynamically adding or removing verification factors based on potential threats.
Choosing Your Digital Security Champion:
Now, the critical question: which method is right for you? It depends on your individual needs and the sensitivity of the information you’re protecting:
- Low-risk accounts: For social media or online shopping, 2FA with phone verification or an app might suffice.
- Medium-risk accounts: Consider enabling 2FA with a hardware key for email accounts or online banking with moderate transaction amounts.
- High-risk accounts: For financial accounts, healthcare portals, or work documents containing sensitive information, MFA with a combination of factors, including biometrics and hardware keys, is strongly recommended.
Actionable Tips for Maximum Security:
Remember, security is an ongoing journey, not a one-time fix. Here are some practical steps you can take to maximize your defenses:
- Enable 2FA/MFA wherever possible: Every additional layer counts, even for seemingly low-risk accounts.
- Embrace strong, unique passwords and change them regularly: Don’t use the same password across multiple platforms, and consider using a password manager for secure storage.
- Beware of phishing scams: Be cautious of suspicious emails, texts, or websites that attempt to trick you into revealing your login credentials.
- Stay informed about evolving threats: Regularly update your software and operating systems to patch vulnerabilities and address new security risks.
- Educate yourself and others: Sharing knowledge is key to building a more secure digital environment. Raise awareness among your friends, family, and colleagues about the importance of online security.
Remember, you have the power to control your online security. By understanding the differences between 2FA and MFA, choosing the right authentication method, and implementing these valuable tips on your social handlers such as tiktok or other social media handlers,you can build a robust shield against cyber threats and navigate the digital world with confidence. Let’s work together to create a more secure and empowered online community
